How to Build a HIPAA-Compliant App

Needless to cite reasons, Healthcare has always been one of the fastest growing business sectors in the world irrespective of economy’s health. As per research, Despite the negative impact of Covid-19 in other business sectors, healthcare spending has remained remarkably stable at the global level and is forecasted to grow by 5.8% to reach USD 8.8 trillion in 2021 and over USD 12 trillion in 2024.
In the world of the ‘web’, healthcare services dealing with sensitive data have to equip themselves with advanced technologies. These healthcare service platforms have to keep up with digital evolution as well as abide by the compliances laid out for the sole purpose of safeguarding sensitive & personal information. The Health Insurance Portability and Accountability Act or (simply) HIPAA is one such compliance.
In simple terms, HIPAA is a set of rules that ensures privacy and confidentiality of your health data by making it inaccessible without your permission, ultimately protecting it from being used for fraudulent activities.
Now since data is GOLD the question is not why you need HIPAA compliant app development but how to go about it.
Reading technical jargon on laws or compliances can be laborious and confusing. Well, leave that to us! We have tried to simply explain the HIPAA rules below that will help you comprehend HIPAA requirements easily.
Let’s get started!
- What is HIPAA?
- Which medical apps need to comply with HIPAA rules?
- What makes HIPAA compliance important?
- HIPAA Rules
- The Security Rule
- 10 Steps for achieving HIPAA compliance
- Other Regulatory Compliances
- Conclusion
What is HIPAA?
The Health Insurance Portability and Accountability Act (HIPAA) was enacted in 1996, with the aim to regulate user/patient data protection, reduce healthcare costs and protect health insurance coverage for those who lose or change their jobs.
The transition from papers to drives, and from drives to cloud, was quick only because of the sheer volume of data that healthcare providers have to deal with on a daily basis. Moving to the cloud enabled effective data management and easier data access by users, be it on phone or on desktop, at home or at office.
But because of this accessible sensitive information, the prime focus of healthcare technology has to be data privacy and protection. This is where HIPAA comes into play.
HIPAA compliant apps ensure privacy and security of patient information, and scrutinizes limitations of health insurance coverage. As healthcare software developers, we develop HIPAA mobile apps that are secure and in accordance with all compliances.
Which medical apps need to comply with HIPAA rules?
Whether an app will be regulated by HIPAA is dependent upon the following two aspects:
- Data covered by the app – PHI
- Entities using the app – Covered Entities & Business Associates.
Let’s understand these two aspects in detail.
PHI or Protected Health Information is any
- individually identifiable health information
- that is created, collected, stored, used or transmitted by a covered entity or its business associate
- in any form, including electronic, paper, or oral.
Health Information includes past, present, and future information about mental and physical health and the condition of an individual, the provision of healthcare to an individual, and information related to payment for healthcare. Health information also includes demographic information about an individual.
Individually identifiable health information, as the name suggests, is health information that can be linked to a specific person, or can be traced back to a particular person. Such patient information includes name, location, phone number, email address, social security numbers, bank account details, photograph, biometric identifiers, Health insurance beneficiary numbers, etc.

Covered Entities are individuals, entities or institutions that transmit PHI for transactions.
These entities shall be governed by HIPAA only if they are responsible for electronically conducting administrative and financial transactions.
The following are classified as covered entities-
Health Plans
- Health insurance companies,
- Health maintenance organizations,
- Government programs that pay for healthcare (Medicare for example),
- Military and Veterans’ health programs.
Healthcare Providers
- Clinics
- Doctors
- Psychologists
- Nursing homes
- Chiropractors
- Dentists
- Pharmacies
Healthcare Clearinghouses
Any entity, public or private, that facilitates the processing of nonstandard healthcare data into standard data format, such as electronic standard, on behalf of other organizations.
Business Associates can be an individual or company that provides services to a HIPAA-covered entity (as defined above) which requires them to use PHI.
Common examples include Software service providers, billing firms, cloud storage providers, lawyers, accountants, email encryption providers, medical device manufacturers, etc.

Prior to a business associate being given access to PHI, they must enter into a Business Associate Agreement (BAA) with the covered entity that describes the responsibilities of the business associate with respect to HIPAA and PHI.

When are you exempt?
Apps that deal with Consumer Health Information do not fall under the umbrella of Hipaa. For example, if your app monitors daily calorie count, weight loss, steps taken in a workout, heart rate, blood pressure or blood sugar readings, you will not need hipaa compliance as long as there’s no personally identifiable user information attached. Hence, apps like Google Fit, MyFitnessPal are exempt.

As soon as you add the person’s name or address or photo to such information, it becomes PHI.
What makes HIPAA compliance important?
Before moving to HIPAA rules, let us first understand why is it so important to comply with HIPAA guidelines from the perspective of both patients and healthcare service providers.
Patient
HIPAA not only serves to protect privacy of sensitive information but also upholds user rights and effectively controls any incident of violation. This compliance is important for patients’ interest as it deals with 4 key aspects
- Privacy
HIPAA ensures privacy of patient data by restricting individuals from accessing or sharing healthcare information without prior permission from the patient. This allows a patient to determine who can view, access and share their information, preventing unauthorized access and limiting any chance of misuse. - Security
HIPAA ensures security of patient’s health data by compelling healthcare organizations to implement safeguards for any medical data that is created, stored or transmitted. This prevents breach of confidential healthcare information. - Notification of Breach
In case of a breach of medical records, notifications have to be issued to patients, within 60 days of a breach discovery. The patients have the right to take necessary actions to protect their identities and to minimize losses or the chance of falling prey to fraud. - Right to obtain copies of Healthcare Data
HIPAA allows patients to exercise their right to obtain copies of their healthcare information created and/or maintained by healthcare organizations so that:
a) They can play an active role in their own healthcare
b) Share information with other healthcare organizations
c) Check for errors in their health records to avoid wrong diagnosis and seek the best possible treatment.
Healthcare Service Providers
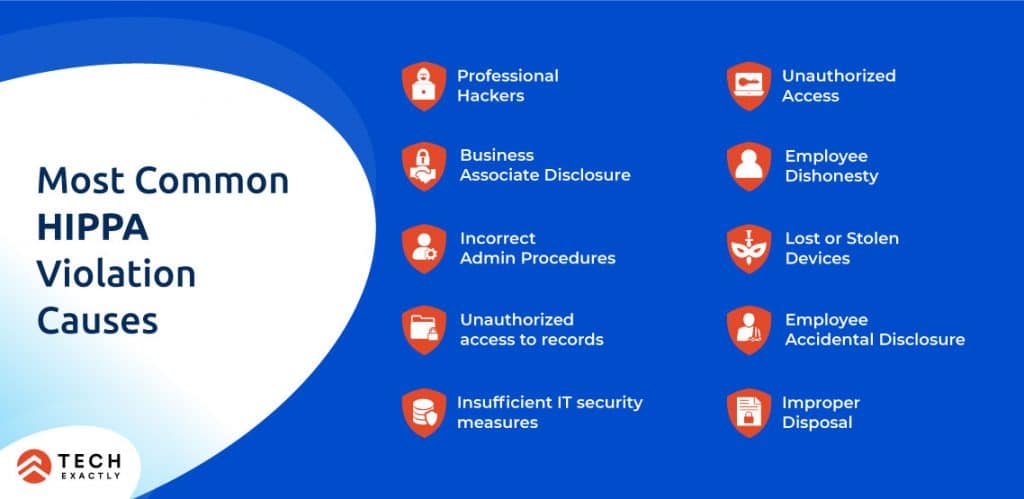
Not only does violation of HIPAA regulations invite jail time, hefty penalties or fines, they also strike a heavy blow to a healthcare service provider’s reputation and trust quotient.
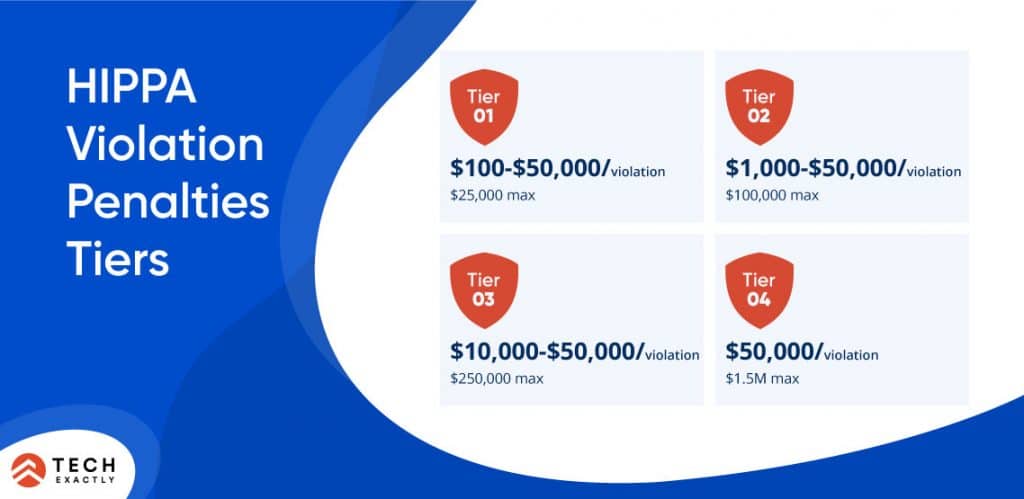
Just in case you’re wondering if it has ever happened, here are some real-life incidents:
- A cardiac monitoring vendor had to settle for a US$2.5 million settlement after losing an unencrypted laptop containing huge amounts of protected patient medical records.
- In 2016, an orthopedic clinic shared X-ray films for digital conversion without signing a BAA with the vendor- a clear violation of HIPAA. They were fined US$750,000 by OCR.
- A doctor’s license was suspended and revoked by the State of New Jersey when it was revealed that his employees regularly forwarded patient bills to a collection firm; the bills had protected information that exposed patient diagnosis details
- A hospital worker from Texas was sentenced to 18 month jail term for wrongfully disclosing patient medical information.
- A cardiology group of physicians and staff were made to pay US$100,000 in 2017 after they had posted clinical and surgical appointments on an unsecure, unencrypted online calendar.
and many more!
HIPAA Rules

HIPAA Privacy & Security Rule establishes national standards to protect the privacy & security of an individual’s Personal Health Information in all formats (including electronic form). It sets limits & conditions on the uses & disclosure of such information without patient authorisation.
HIPAA Enforcement Rule explains how companies need to handle HIPAA violations. It contains provisions relating to compliance and investigations, the specifications for a Civil Monetary Penalty (“CMP”) that may be imposed for HIPAA violations and procedures for hearings.
HIPAA Breach Notification Rule requires organizations that experience a PHI breach to report the incident. Depending on how many patients are affected by the breach, reporting requirements differ.
Keeping healthcare app/software development in mind, we will study the Security Rule in detail.
The Security Rule
The HIPAA Security Rule extends the HIPAA Privacy rule to include electronic protected health information (ePHI). This rule requires covered entities & business associates to implement security measures, at all times, to protect ePHI from misuse. This is done by complying with three categories of safeguards as defined by the rule:
- Administrative
- Technical
- Physical.
Covered entities & their BA’s have to assess security risks, and put in place these safeguards to ensure security, confidentiality and integrity of patient data.
Administrative Safeguards pertain to processes, policies and procedures that work to protect ePHI from a breach and also manage conduct of employees in relation to protection of this information. The Security Rule places major emphasis on administrative safeguards, as they lay down the foundation for compliance with physical and technical safeguards that follow. This safeguard can be implemented using the following standards:
- Security Management Process – Have procedures in place to prevent, detect and correct security violations. Guide your employees to identify vulnerabilities & potential breaches and how to manage such risks. Also, you must have internal policies to penalise employees found violating guidelines for safeguarding ePHI.
- Designate an individual as your Privacy Officer who will develop and implement security policies and procedures for your organisation. Number of Privacy Officers will depend upon the size & complexity of your organisation.
- Workforce security – Govern employee access to electronic information, through supervision, authorisation, clearances and termination. Ensure that whenever an employee exits/changes roles, his permissions are updated accordingly.
- Manage information access to limit unnecessary or inappropriate access to & disclosure of PHI and consequent security breaches. As part of this procedure, you must determine how & who to grant access to ePHI, add/remove accesses, whenever necessary, etc.
- Your organisation must have HIPAA Security Awareness Training Programs for all employees, to educate them about the importance of security, safeguarding their passwords, reporting in case of breach, etc.
- Ability to identify security incidents for prompt reporting and tackling of security issues by employees.
- Develop contingency & business continuity plans in case of a natural disaster including recovering access to ePHI, enabling emergency mode operations & establishing daily data backup systems.
- Periodically evaluate your procedures, plans and policies to avoid non-compliance of HIPAA regulations
- Before sharing or transmitting ePHI, have a Business Associate Agreement (BAA) signed with your BA clearly stating how ePHI will be shared, used & protected. This will help you protect your organisation in case of a breach.
Technical Safeguards are standards related to technology that is used to protect & control access to electronic protected health information (ePHI). To safeguard confidential data from unauthorised access, modification and misuse, PHI should be encrypted always, whether at rest or in transit. This will ensure that even if PHI has been accessed illegally, it cannot be decoded & misused. A few areas that need attention are Access Control, Audit Controls, Data Integrity, Individual Authentication, Data Transmission.

Physical Safeguards focus on securing devices and facilities that store PHI, such as computers, data centers, servers, etc from natural and environmental hazards, and unauthorized intrusion. It is imperative to perform a complete risk assessment of your existing infrastructure. Some of the elements that need to be reviewed are Facility Access Controls, Workstation Use, Workstation Security, PHI storing Device & Media Controls.
We will study each of these areas in the following section.
10 Steps for achieving HIPAA compliance
1. Controlling Access to PHI
The HIPAA Privacy Rule clearly states that access of patient information should be based on clearance level and requirement. By assigning unique identity and privileges to users, the rule safeguards data by restricting unnecessary access. A few ways to control access are:
- Assigning a unique ID to each user which will help to track & identify the activity of every user.
- Creating a list of privileges raging from ‘View Record’, ‘Edit Record’, ‘Create New Record’, ‘Delete Record’.
- Assigning these privileges to different groups of users in accordance with the role/position in the organisation, say, doctors, lab technicians, admin, etc.
2. Proof of Identification for Authenticity
Once a unique ID is assigned and role based accesses have been given, it is important for the system to verify that the person trying to access PHI is the one he/she claims to be. This can be implemented, say, in the form of:
- Login password,
- One Time Password,
- Biometric Data,
- Smart token
Multi-factor authentication will give you extra security. However, in case of an emergency, a user should be allowed access to ePHI beyond their clearance, but this should be followed by an immediate review procedure.
3. Automatic time-out
Your system should be pre-programmed to automatically close a session after a set period of inactivity. To access his/her account, the user will again have to log in. This will help PHI from being mishandled in case the app is unattended or the device is lost, which will significantly improve security.
4. Activity Tracking & Audit Controls
Audit control standards compel developers to implement mechanisms that examine the activities of systems storing or using PHI. A few points to remember:
- Monitoring what is done to the PHI stored in your system via software, hardware, or procedural means.
- Recording login & log out of each user
- Being aware of who, when and where the sensitive data was accessed, updated, modified or deleted. All changes must be supported by evidence.
- Maintaining log files which should be audited periodically to restrict misuse of information and abuse of privileges.
5. Encryption
Encryption is the best way to keep your data safe. It is achieved by creating a cocoon of codes that requires a decryption key to convert the data in human-readable format. You may use RSA and AES algorithms with strong keys or encrypted databases like SQLCipher for safely storing the data in the backend.
6. Secured Transmission of Data
HIPAA mandates health data encryption in transmission. This can be achieved by using HTTP protocols, Secure Sockets Layer (SSL), Transport Layer Security (TLS), or even Advanced Encryption Standard (AES). Again, encryption here is of utmost importance to safeguard sensitive data from man-in-the-middle (MitM) attacks.
7. Careful Disposal of PHI
PHI should be immediately and permanently destroyed, when not needed anymore. It is very common for a copy of PHI to be hidden in unexpected places like USB, Floppy Disks, memory cards, portable devices like hard drives or laptops, in photocopiers, scanners, etc. This requires you to be mindful of erasing such data from all places for it to be considered ‘disposed of’.
8. Securing the Hardware
Accessing PHI remotely from a phone or laptop is as vulnerable as convenient. Hence, it is fundamental that all devices that access ePHI should be encrypted. Safeguard machines with antivirus protection, firewalls, VPNs, SSL Certificates, and related technologies. A few ways to achieve hardware security are:
- Securely place servers and PCs in a safe location,
- Have your workplace under Video Surveillance
- Doors, Windows & WorkStation locks to guard against theft.
- Workstation security measures to restrict access to authorized users
- Have every employee delete ePHI records from their devices when they exit from your company.
- Never share PHI over push notification as it is visible on screen even if the receiver’s phone is locked.
9. Data Backup
PHI is too valuable to lose from either physical damage, server failures or data tampering. Hence, to establish data integrity, it is imperative to have backup that is retrievable. Multiple backups stored in encrypted hardware or secured data cloud helps in protection of invariably sensitive data. It would be wise to develop disaster recovery & business continuity plans.
10. Testing and Maintenance
Testing and maintenance are two of the most important processes that ensure stability & efficiency of sophisticated platforms.
Maintenance is an ongoing process to ensure your applications are safe, stable and free of bugs, breaches and crashes.
After you have built an app, it is important to regularly update them, And after every update, or periodically, you must test run your processes, to ensure its working smoothly.
Other Regulatory Compliances
As a healthcare service provider, you have to be aware of compliances other than HIPAA. Depending on your geographical or operational location you’ll have to meet other standards as well. Here are some fundamental compliances-
- U.S. Food and Drug Administration (FDA)
- Health Information Technology for Economic and Clinical Health Act (HITECH)
- Health Level Seven International (HL7) in US
- General Data Protection Regulation (GDPR) in EU
- Data Protection Law Enforcement Directive in EU
- Personal Information Protection & Electronic Documents Act in Canada
- Data Protection Act (DPA) in UK
Conclusion
Healthcare applications and software are the way forward. While improving real-time care and ease of functioning, the digital transformation of healthcare has mandated safeguarding of patients’ interests. It is imperative that healthcare organizations and service providers seek the best consultation and service for healthcare app development, from experts with comprehensive compliance strategies. We, at Tech Exactly, deliver the best technological solutions for building healthcare service platforms that boost security, privacy and dependability. With extensive experience to strategize compliances for app & software development you can expect nothing but the best platform for your operations.
